The smart Trick of Aws Backup That Nobody is Discussing
Wiki Article
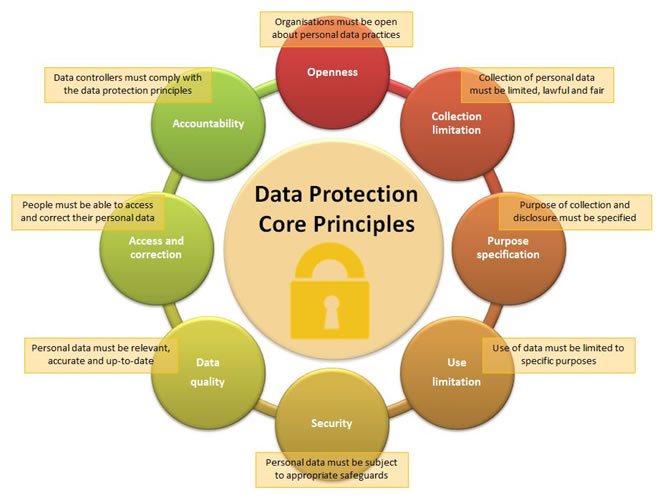
Get This Report about Data Protection
Table of ContentsThe 10-Second Trick For Ec2 BackupEverything about Data ProtectionAws Backup for DummiesRumored Buzz on RtoProtection Against Ransomware for DummiesSome Ideas on S3 Backup You Need To Know
Information security is the procedure of protecting important info from corruption, compromise or loss - https://www.wikicraigs.com/author/clumi0/. The significance of information security boosts as the quantity of information developed and saved remains to expand at unprecedented prices. There is likewise little tolerance for downtime that can make it impossible to accessibility important information.Securing information from compromise and ensuring data personal privacy are various other essential parts of information security. The coronavirus pandemic created countless staff members to work from residence, causing the demand for remote data protection (http://peterjackson.mee.nu/where_i_work#c1508). Organizations should adjust to guarantee they are securing information anywhere employees are, from a central information facility in the workplace to laptops in your home.
The key principles of data protection are to guard and provide information under all conditions. The term data defense describes both the operational backup of data in addition to business continuity/disaster healing (BCDR). Data security techniques are progressing along two lines: information availability as well as information management. Information accessibility makes certain individuals have the data they need to perform service even if the information is harmed or lost.
Information lifecycle management is a comprehensive strategy for valuing, cataloging and also protecting info assets from application as well as user errors, malware and also virus strikes, maker failure or center blackouts as well as disruptions. Extra lately, information administration has actually come to include locating methods to unlock service value from otherwise dormant copies of information for reporting, test/dev enablement, analytics as well as various other purposes.
The S3 Backup PDFs
Storage snapshots can immediately create a collection of tips to info stored on tape or disk, enabling faster information recuperation, while constant information defense (CDP) backs up all the data in a business whenever a change is made. Information portability-- the capacity to relocate information amongst different application programs, calculating atmospheres or cloud services-- presents one more set of troubles as well as solutions for information defense.
Data was periodically duplicated, generally each night, to a disk drive or tape collection where it would sit till something went wrong with the key information storage space. That's when organizations would certainly access and also make use of the backup information to bring back shed or harmed information. Backups are no more a standalone feature.
How S3 Cloud Backup can Save You Time, Stress, and Money.
Backup's function was to bring back information after a failure, while an archive provided a searchable copy of information. That led to repetitive information sets.
Pictures as well as duplication have actually made it possible to recoup much faster from a catastrophe than in the past. When a web server fails, information from a backup variety is utilized in location of the key storage space-- but just if an organization takes actions to stop that back-up from being modified.
The original information from the back-up range is then made use of for checked out operations, as well as compose operations are guided to the differencing disk. This technique leaves the original back-up data unchanged. As well as while all this is occurring, the fallen short web server's storage is rebuilt, as well as data is reproduced from the back-up variety to the stopped working web server's newly restored storage space - https://www.metal-archives.com/users/clumi0.
Not known Facts About Protection Against Ransomware
Information deduplication, likewise understood as information dedupe, plays a vital role in disk-based back-up. Dedupe applications replace redundant information blocks with pointers to one-of-a-kind data copies.Deduplication began as an information security modern technology and has relocated right into primary information as an useful attribute to decrease the amount of capability required for much more pricey flash media. CDP has come to play an essential function in calamity healing, and it enables quick recovers of backup information. Constant information security makes it possible for organizations to roll back to the last good duplicate of a documents or database, lowering the quantity of information lost when it comes to corruption or data deletion.
CDP can likewise get rid of the requirement to keep numerous duplicates of data. Instead, companies keep a single duplicate that's updated continually as changes take place.
Synchronous matching is one approach in which information is contacted a neighborhood disk and also a remote site at the same time. The compose is not thought about complete till a verification is sent from the remote site, making sure that both sites are constantly similar. Mirroring requires 100% ability expenses.
The Only Guide for Ec2 Backup

The expense of recouping from a media failing is the moment it requires to return to a safeguarded state. Mirrored systems can return to a safeguarded state swiftly; RAID systems take much longer since they have to recalculate all the parity. Advanced RAID controllers don't need to read a whole drive to recoup information when doing a drive restore.
Considered that the majority of drives perform at regarding one-third capacity, smart RAID can reduce recovery times dramatically. Erasure coding is a different to advanced RAID that's often used in scale-out storage settings. Like RAID, erasure coding uses parity-based data security systems, creating both information as well as parity throughout a collection of storage space nodes.
Replication is another information defense choice for scale-out storage, where data is mirrored from one node to one more or to numerous nodes. Replication is simpler than erasure coding, however it eats a minimum of two times the capacity of the protected information. With erasure coding, data is saved throughout various disks to shield against any solitary factor of failing.
The 8-Minute Rule for Protection Against Ransomware
Most storage systems today can track thousands of pictures without any type of significant impact on efficiency. Storage systems utilizing pictures can deal with platforms, such as Oracle as well as Microsoft SQL Server, to catch a tidy copy of information while the photo is taking place. This method makes it possible for constant snapshots that can be kept for long periods of time.With this technique, minimal data is shed and recovery time is virtually instant. To protect against several drive failures or some other significant event, information facilities rely upon duplication modern technology improved top of snapshots. With photo duplication, just my review here blocks of information that have actually transformed are duplicated from the primary storage space system to an off-site secondary storage system.
Report this wiki page